Security Operations Services
Secure Your Infrastructure with Expert Security Operations
Round-the-clock security operations help detect, respond to, and prevent threats before they cause damage. With real-time monitoring, quick incident handling, and strong compliance practices, these services reduce risk and keep your systems stable and protected in a constantly changing environment.

Our Services
24/7 Security Monitoring
We monitor your systems 24/7 for threats—delivering real-time alerts and protection to keep your business secure.
Our Priorities
Trusted Security, Backed by Leading Certifications
Our security practices are built on industry-recognized standards and backed by leading certifications. From data protection to operational controls, we follow strict guidelines to keep your systems secure and compliant—giving you the confidence to focus on your business.
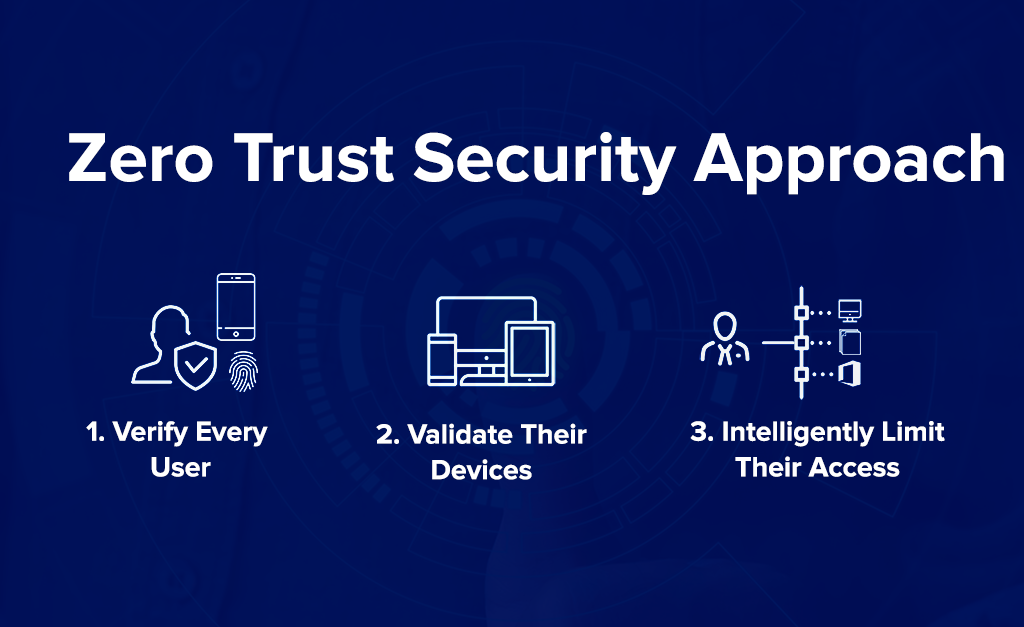

Why Choose Security Operations Services for Your Next Project
Benefits of Security Operations Services
- 24/7 Threat Monitoring : Continuous system oversight ensures threats are identified early, reducing the risk of escalation or disruption.
- Rapid Incident Response : Swift action in the event of a breach helps minimize downtime, data loss, and business impact.
- Enhanced Risk Management : Proactive identification and remediation of vulnerabilities strengthen your overall security posture.
- Regulatory Compliance Support : Maintain alignment with key industry standards and avoid costly compliance violations.
- Improved System Reliability : Consistent monitoring and maintenance help ensure stable, uninterrupted operations.
- Confidence and Peace of Mind : Rely on an experienced security team dedicated to protecting your infrastructure around the clock.

FAQs Security Operations Services
What are Security Operations Services?
Security Operations Services encompass the continuous monitoring, detection, and response to cyber threats. These services are designed to protect IT environments, reduce risk, and support regulatory compliance through structured security practices.
Is 24/7 monitoring necessary for my business?
Yes. Threats can emerge at any time, and around-the-clock monitoring ensures immediate detection and response. This minimizes the risk of data breaches, downtime, and financial loss.
Which industries benefit from Security Operations Services?
Organizations in finance, healthcare, retail, legal, and any sector handling sensitive data or subject to regulatory standards benefit significantly from these services.
Do these services assist with compliance requirements?
Yes. Security Operations Services support compliance with regulations such as GDPR, HIPAA, ISO 27001, and SOC 2 by maintaining logs, enforcing policies, and documenting security incidents.
How are security incidents managed?
Each incident is assessed, contained, and resolved through a structured response process. Clients receive a full incident report detailing the root cause, resolution steps, and recommendations to prevent recurrence.
Can these services integrate with our existing tools and infrastructure?
Absolutely. Our approach is flexible and designed to work alongside your current systems, enhancing your security posture without disrupting operations.
Are these services suitable for small and mid-sized businesses?
Yes. Security Operations Services are scalable and valuable for organizations of all sizes. Small and mid-sized businesses benefit from professional security coverage without the cost of building an in-house team.
